More than sales proposal software
Elevate your sales game with interactive proposals.
Stand out with personalized proposals, quotes and contracts delivered as engaging web pages. Get notified when a buyer takes action.
No credit card required | 14 day free trial
Loved by 4000+ customers









How it works
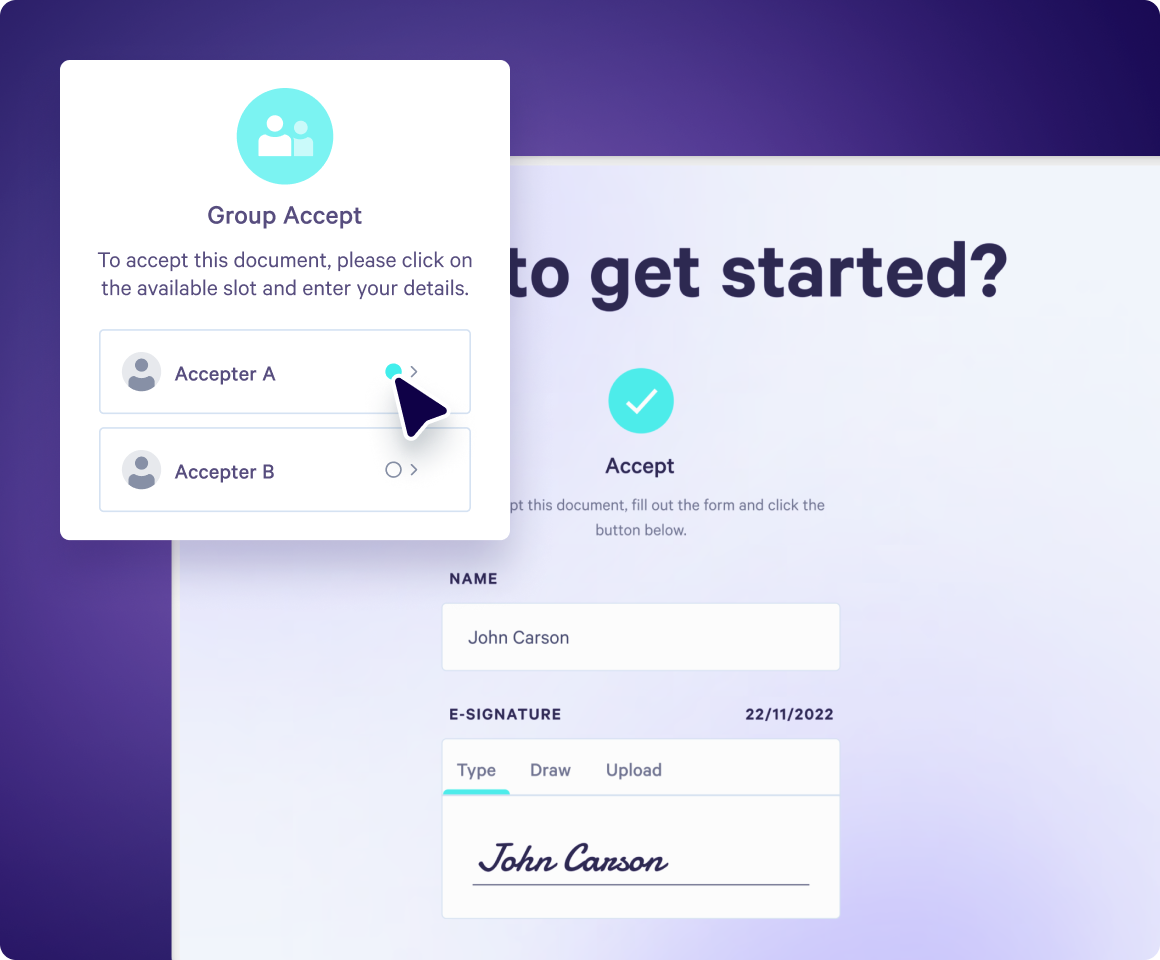
Software overview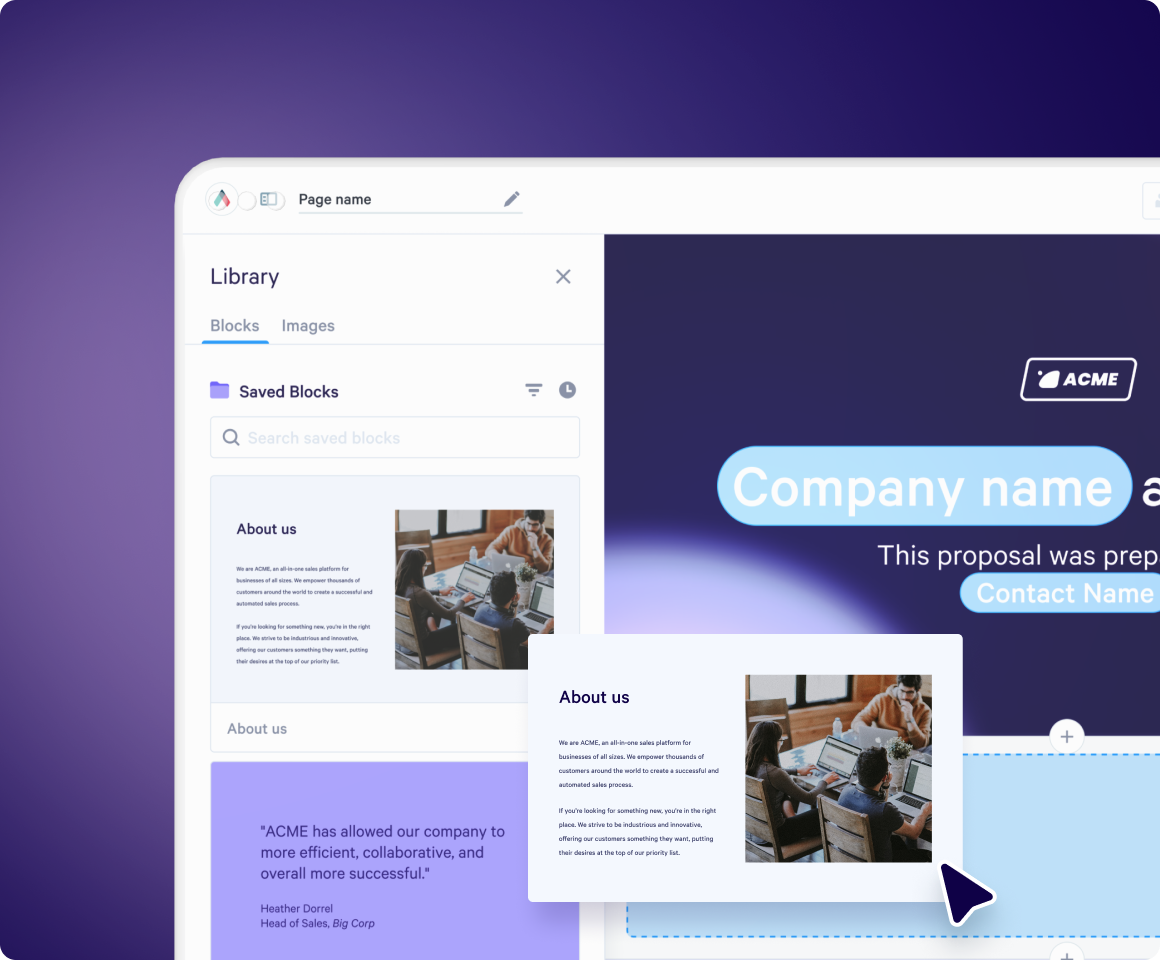
Connected with the best
Qwilr integrates with all the leading CRM, sales and accounting software, like HubSpot, Salesforce, Zoho, Pipedrive, and Quickbooks.
Build your first page with AI
Create ready to go proposals, quotes and contracts in a few clicks.
Try one of these ✨
Qwilr drives revenue for sales teams
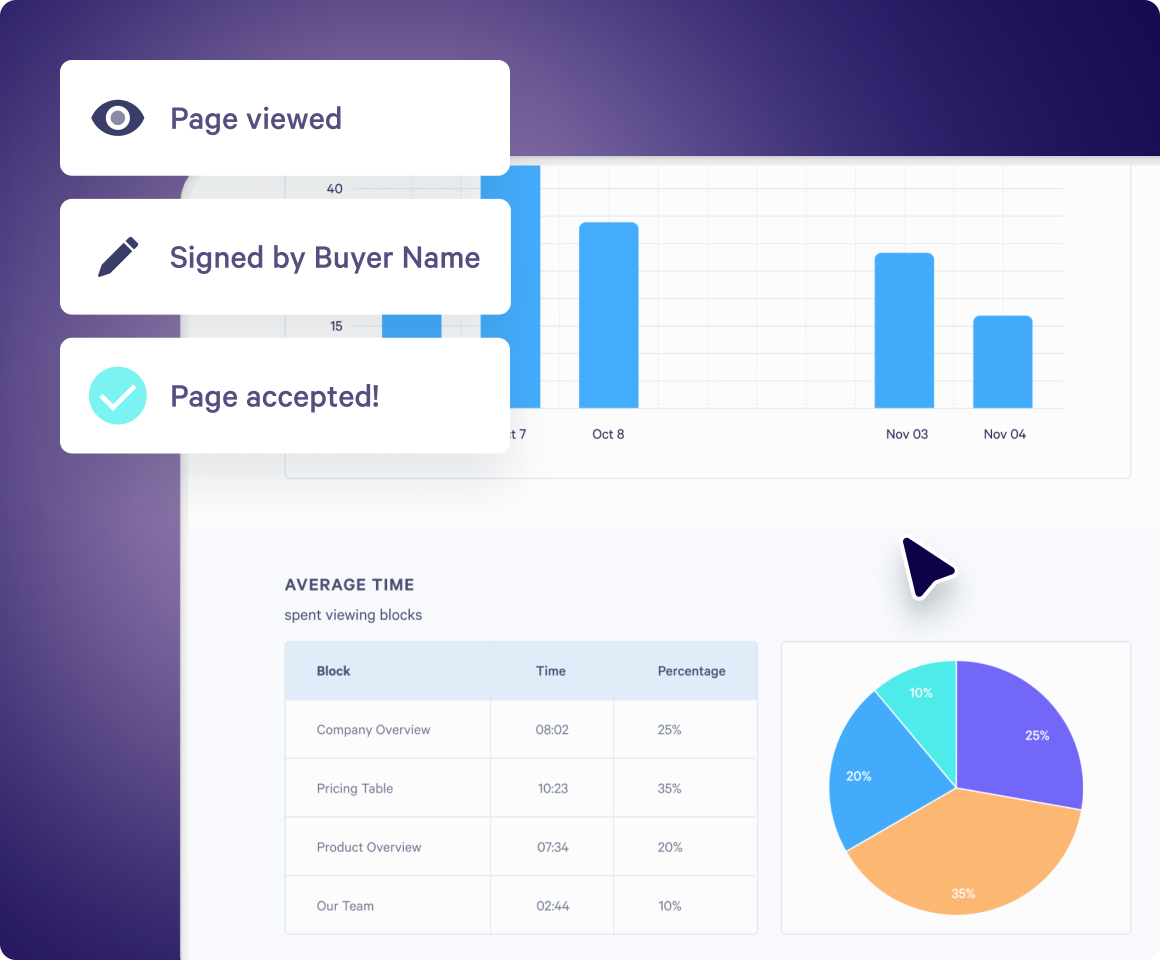
With Qwilr, your sales team unlocks revenue with insights into how buyers are engaging with your content at crucial stages of the deal.
500+ 5-star G2 reviews
Win rate
Increase in win rates with Qwilr.
ROI
To see full payback.
Time saved
Reduction in time to close deals.
Reduction in time spent creating sales materials.
Teams love Qwilr
Use Qwilr across all your GTM teams to build an end-to-end sales experience that increases deal velocity.

Sales leaders
Empower your team and increase your revenue.

Marketing
Create beautiful collateral consistently that you can track.

Sales operations
Build a scaleable and personalized quoting system.

Customer success
Deepen customer relationships with personalized content.
A word from our customers



Qwilr has been a game-changer for us. Sales collateral that used to be a pain to build in Slides/Docs can now be spun up with Qwilr in minutes. Plus, we get real-time reporting to know when a prospect has re-engaged or is sharing our materials internally.



“Qwilr has saved each sales rep an average of 1 hour per deal closed. Since implementing Qwilr, we have closed over 2,000 deals, saving us over 2,000 hours of time that we can invest in additional sales activities.”



“I love the live link. It’s been really helpful to be able to make changes on the fly and not have to resend a bunch of documents. It’s a much better customer experience than someone needing to look through multiple versions to find the most current one.”



“Sometimes, we’re not even able to get in the room. Our proposal has to be the representation of the salesperson and have all the information a customer needs because our product is complex.”



“On a functional level, we really appreciate how Qwilr allows us to password protect and digitally sign our proposals to improve privacy and security with clients. Also, the ability to track page views on live proposals has helped us better focus our time and efforts on pursuing quality leads.”



“We’re seeing deals close a lot faster while also adding a level of professionalism and enjoying powerful insights. None of these things we were getting through the use of PDFs and e-signature software alone.”
Templates for all needs
Explore proposal templates and collateral for sales, marketing, customer success, sales enablement, and more.
Explore template gallery










